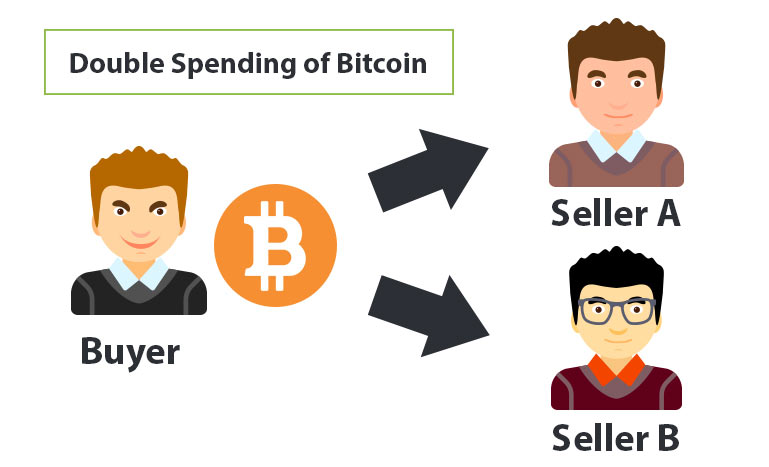
It is impossible to double spend fiat currency because only a certain amount of cash exists. And, you can’t spend the same banknote in two different places at the same time. However, you could theoretically send the same digital code and signature to two different people at exactly the same time – this is the Double Spending Problem.
If digital money could be counterfeited, it would become worthless. This is called a double spending problem, and Bitcoin is the first protocol to solve the problem. Since digital currencies are only stored electronically, it might seem easy to copy a file, which would make duplication intrinsically difficult to prevent. This would definitely have implications on the value of a digital currency since the potential to duplicate transactions would invalidate its entire ecosystem. This problem is known as double spending.
What is the Double Spending Problem?
The Bitcoin technical glossary gives the following definition to double spending: it is a transaction that uses the same input as an already broadcast transaction. The attempt of duplication, deceit, or conversion, will be adjudicated when only one of the transactions is recorded in the blockchain. In other words, double spending means spending the same money twice.
If you go to the nearest coffee shop and spend $10 there, you pay in cash. As you paid with your $10 bill, the service provider instantly confirms your payment, and you receive your coffee in exchange for the money. So now you cannot spend the same $10, as you don’t own them anymore.
However, Bitcoin is a digital cryptocurrency, not physical cash. Hence, it is possible for a BTC transaction to be copied and rebroadcast. This opens up the possibility that the same BTC could be spent twice by its owner.
When you pay cash, your payment is confirmed and verified instantly by another human. But with digital currency like BTC, if this verification mechanism is missing, it can lead to double spending. Anyone can just copy that digital money and pay somewhere else. That’s why we need the Blockchain to prevent the Bitcoin from being double spent.
Blockchain
Blockchain protocols are basically a form of governance. A blockchain governs a ledger of data, for example transaction data. Because the blockchain software can govern this for us, we no longer need a third party, such as a government or bank, to do it. This is what makes (most) blockchains decentralized. The protocol of the Bitcoin blockchain is based on democracy, meaning that the majority of the participants (miners) on the network will get to decide what version of the blockchain represents the truth.
When a transaction is taken out of the unconfirmed transactions pool and put into the blockchain they are checked for validity. So let’s say transaction A is pulled out of the pool. It seems to be valid (since I have one BTC) and it is inserted into the blockchain. Now transaction B is pulled out of the pool. It is invalid since I don’t have Bitcoins to spend and it does not get confirmed. But what if the validation process of A and B happened simultaneously? Meaning both transactions show that I have the money. In this case, we will have 2 branches of the blockchain and a race will begin – the first one to achieve the next block of confirmations will win. If they reach the next block simultaneously as well, we will have another race and so on. This is why it’s recommended to wait for 6 confirmations before considering a transaction complete. It’s highly unlikely that this race will happen more than 6 times. So in the end we will have a clear winner and only one transaction will be confirmed. Until this race is resolved, both transactions are at risk of being canceled.
How to Double Spend Bitcoin?
A double spend is where two different transactions sent into the Bitcoin network are trying to spend the same account balance. Bitcoin naturally prevents this by confirming which transaction is included in a block first.
If two transactions are sent into the network using the same private key and the same funds but sent to different addresses, then as the transaction propagates through the network, one half of the network will accept one transaction, and the other half, the other.
The situation is resolved by which side of the network resolves one of the two transactions into a block first.
So if you try and spend your coins twice – once to a merchant and once back to another address under your control, then you will have roughly a 50% chance of regaining your money and getting the product for free (if chance favors your address as being the Bitcoin networks consensus).
This, though, depends on which transaction gets propagated further into the network. For example, if transaction A reaches ten mining nodes controlling 80% of the network hashing power first and the other transaction only reaches 20%, then transaction A will have an 80% chance of being included in the next block and becoming the confirmed transaction.
Double Spending Attack
When people attempt to intentionally take advantage of this vulnerability, it is referred to as a ‘double spend’ attack.
A 51% attack or double-spend attack is a miner or group of miners on a blockchain trying to spend their crypto’s on that blockchain twice. Bitcoin is secured by having all miners (computers processing the networks transactions) agree on a shared ledger called the blockchain. Bitcoin nodes look to each other to verify that what they’re working on is the valid blockchain. If the majority of miners are controlled by a single entity, they would have the power to (at least attempt to) decide which transactions get approved or not. This would allow them to prevent other transactions, and allow their own coins to be spent multiple times.
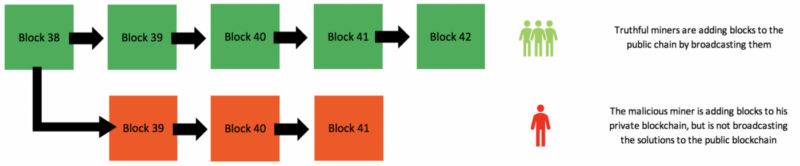
The attackers would be able to prevent new transactions from gaining confirmations, allowing them to halt payments between some or all users. They would also be able to reverse transactions that were completed while they were in control of the network, meaning they could double-spend coins.
However, hitting 51% network control is not a guarantee of success, it’s just the point where success is likely. It is an interesting concept because it is theoretically possible, the network is free and open, so if someone were to have enough computational power (which would cost a huge amount of money), there is no Bitcoin authority to stop them from doing so. In the event that such an attack successfully takes place, confidence in the currency would be lost and its value would disintegrate.
In reality these attacks are extremely hard to perform. As was mentioned above, a miner would need more hashing power than the rest of the network combined. Considering the fact that there are millions of miners on the Bitcoin blockchain, a malicious miner would have to spend enormous amounts of money on mining hardware to compete with the rest of the network. Even the strongest computers on earth are not directly competitive with the total computational power on this network. And there are countless other roadblocks to performing a 51% attack. For example, the risk of getting caught and prosecuted, electricity costs, renting space and storage for all the mining hardware, covering your tracks and laundering the money. An operation like this is simply way too much cost and effort for what the attacker might get in return, at least in the case of the Bitcoin blockchain.
They would almost certainly not be able to create new coins or alter old blocks, so a 51% attack would probably not destroy Bitcoin or another blockchain-based currency outright, even if it proved highly damaging.
How Does Bitcoin Prevent Double Spending?
In the past, double spending in electronic transactions could only be avoided through the use of a central third party.
Bitcoin was the first platform to solve the double spend problem without the use of a third party, and did so through the invention of what is now referred to as blockchain technology. Blockchain gets its name from the way in which transactions occur on the network. All transactions are handled in ‘blocks’ which are then sequentially added to the chain.
Although Bitcoin solves the problem of being copied and getting spent twice, The block chain itself does not prevent double-spending, instead, all transactions posted to the blockchain are verified and protected through a confirmation process. Once a transaction has been confirmed, it is irreversible and is posted publicly.
In Bitcoin terms, a “block” is a file of permanently recorded data. All recent transactions are written into blocks, much like a stock transaction ledger on an exchange. The term “blockchain” refers to a virtual ledger that is publicly (yet anonymously) shared by all members of the Bitcoin network. Any economic transaction involving the Blockchain.info allows users to navigate the Bitcoin blockchain and review transactions in quantity only, information about buyers and sellers are protected. Bitcoin uses a high-level AES encryption to prevent outside sources from accessing or changing the ledger.
All Bitcoin wallets are instantly updated through the blockchain. “The integrity and the chronological order of the blockchain are enforced with cryptography,” as the Bitcoin website indicates.
The blockchain, which is an open and immutable ledger, ensures that transactions are finalized by its inputs confirmed by miners. The confirmations make each unique Bitcoin and its subsequent transactions legitimate. If one tried to duplicate a transaction, the original blocks deterministic functions would change showing the network that it is counterfeit and would not to be accepted.
If you were to attempt to send one hundredth of a Bitcoin to a peer, the transaction would first sit in an unconfirmed pool, waiting to be added to the chain. Once it is time for the block to be transmitted, every computer (or node) in the network then proceeds to verify it.
Here, if double spending were to occur, the first transaction would be added to the blockchain normally, but the entirety of the network would reject the second and subsequent transactions, thus avoiding potential double spending.
There are ways of safeguarding against this – whereby wallet operators (like Electrum Bitcoin Wallet) keep strong links into mining nodes to propagate their transactions fed directly in – so another transaction spending the same output can’t be fed into the network on a fraudulent basis.
Solutions to Double Spending Digital Currency:
1. Proof-of-Work (PoW, used by BTC, BCH, and LTC),
Proof-of-Work, or PoW, is the original consensus algorithm in a Blockchain network. This algorithm is used to confirm transactions and produce new blocks to the chain. With PoW, miners compete against each other to complete transactions on the network and get rewarded. The main working principles are a complicated mathematical puzzle and a possibility to easily prove the solution.
The answer to the PoW problem or mathematical equation is called a hash. As the network grows, it is facing more and more difficulties. The algorithms need more and more hash power to solve. So, the complexity of the task is a sensitive issue. If a miner manages to solve a puzzle, a new block is formed. The transaction is placed in this block and is considered confirmed.
Proof-of-Work is used in a lot of cryptocurrencies. As Bitcoin was the first, it laid the foundation for this type of consensus. The puzzle is Hashcash. This algorithm allows changing the complexity of a puzzle based on the total power of the network. The average time of block formation is 10 minutes. Bitcoin-based cryptocurrencies, such as Litecoin, have a similar system.
Another large project with PoW is Ethereum. Given that almost three of four projects are implemented on the Ethereum platform, it’s safe to say that the majority of Blockchain applications use the PoW consensus model.
2. Proof-of-Stake (PoS, used by Cardano, Stellar, and eventually Ethereum),
The Proof of Stake (PoS) concept states that a person can mine or validate block transactions based on how many coins he or she holds. This means that the more Bitcoin or altcoin owned by a miner, the more mining power he or she has. Users who validate transactions and create new blocks in this system are referred to as forgers.
In order to validate transactions and create blocks, a forger must first put his/her own coins at ‘stake’. Think of this as their holdings being held in an escrow account: if they validate a fraudulent transaction, they lose their holdings, as well as their rights to participate as a forger in the future. Once the forger puts up their stake, they can partake in the forging process, and because they have staked their own money, they are in theory now incented to validate the right transactions.
3. Ripple Consensus Process (RCP, used by Ripple).
In RCP, auditors are explicitly trusted, eliminating the need for them to post collateral while, at the same time eliminating the need for compensation. As a result, they lack most of the motivation to become Leader seen in proof-of-work and proof-of-stake systems. With no payout for Leaders, a very different selection protocol becomes possible.
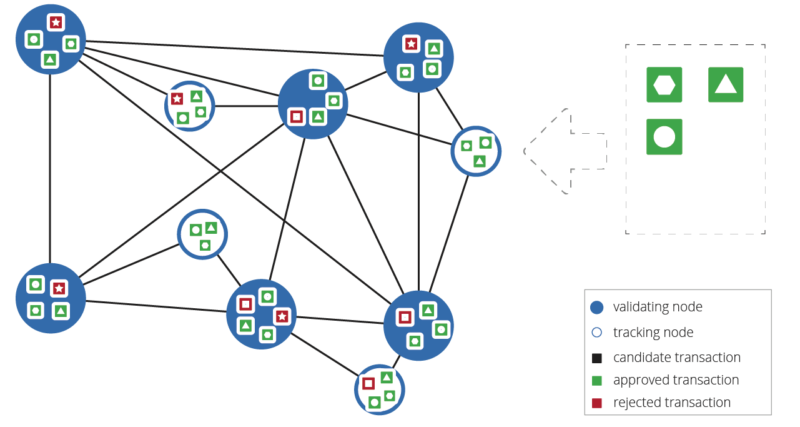
RCP Leader selection begins by each auditor proposing to its trusted peers an update consisting of a set of transactions to be written into the log. After receiving all proposals, an auditor decides which one to use for the next round. Priority is given to those proposals which have supermajority support. In other words, an auditor changes its choice based on whichever proposal gains the most support. This process continues through multiple rounds until a clear supermajority emerges. The threshold for this supermajority is adjustable, but the default used on the Ripple network is 80%.
This process has been called “avalanche” because of the way a single proposal rapidly becomes the preferred choice. The use of avalanche consensus, coupled with the fact that auditors only need to listen to a handful of trusted peers offers the potential for very fast transaction confirmation.
Summary
So now you have a better understanding of double-spending. It is nearly impossible, and hardly profitable, when you factor in all the costs, and the associated risks.