When choosing a Bitcoin wallet, the number of options available might be a bit intimidating, especially for newbies. And, while mobile and online banking are becoming more popular, fully digital payment solutions, like Bitcoin or other cryptocurrencies, are rather intimidating to ordinary people.
When cryptocurrency is stored in a device which is entirely offline, it is considered to be in cold storage. Cold wallets are the best option for those seeking maximum security. They are best suited for long term asset holders who don’t regularly access their crypto assets. The different types of cold storage include hardware and paper wallets.
Today, we are here to compare these two types of storage in order to find the one that is right for you and will meet your needs.
When cryptocurrencies are stored in a device which is entirely offline, it is a form of cold storage. Cold wallets are the best option for those seeking the most secure form of storage. They are best suited for long-term asset holders who don’t require access to their crypto assets for months or even years. The different types of cold storage include hardware and paper wallets.
So today we are good to compare these two types of storage in order to find the one that will meet your expectations.
What is a Hardware Wallet?
Hardware wallet is a physical device created to keep your cryptocurrency safe.
The three most popular ones are KeepKey, Ledger and Trezor. Another product, OpenDime, isn’t technically a hardware wallet because of limited functionality, but it is a cheaper option that has a lot of the same functions. Essentially, it is one-time use storage that will allow you to continually add funds but must be physically destroyed to take the funds out.
The idea behind hardware wallets is to isolate the private keys from online methods of storage, such as a computer or smartphone, which are more susceptible to being compromised by a hacker. Storing your private keys offline prevents against this, as hackers would have to physically steal your hardware device in order to gain access to a user’s private keys. But even then, most hardware wallets require a PIN code for access, providing an added layer of protection.
However, they are not free. But the price can be worth it if you own a significant amount of bitcoins. This device will protect a few hundred in Bitcoin just as effectively as a few million.
Most of the hardware wallets:
- Generate and store on the device a private key
- All the operations and transactions are executed on the device. It can display only the result of it: a hash of each operation.
- Have a screen to display some information
- Have one or more physical buttons
- Display transaction information
- Require a manual confirmation of an operation using a hardware button
- Allow to create a backup of private keys if the device is broken, lost or stolen
- Require to install manufacturer-provided software
- Works on all modern versions of Windows, Linux, Mac OS
- Doesn’t allow to install any software on the device
- Require to set up a PIN code (or even multiple PIN codes)
- Support only a few top cryptocurrencies
Possible Vulnerabilities
There is no information about tokens being stolen from a hardware wallet. However, it’s important to understand that using hardware storage couldn’t be a silver bullet. There are still a few possible vulnerabilities:
- Replacing receiver’s address.
It cannot prevent you from sending your tokens to a wrong address. For example, a virus on your desktop can track your transactions and replace the destination address one it detects a large transaction. To solve this problem, it’s recommended to use a 2 Factor Authentication to confirm a transaction.
- A bad random number generator.
Hardware wallets depend on their intern random number generators. Unfortunately, to generate a real random number isn’t that easy. A bad random number generator can create such values that could be predicted by a hacker.
- Bugs.
The security of any system — hardware or software is based on the quality of its realization. Hardware wallets are not an exception. Firmware bugs could give to an attacker the access to internal structure of a device.
- Compromised manufacturing process.
Even an ideal firmware and hardware can’t prevent from an intentional or an unintentional intrusion during the manufacturing.
- Compromised delivery process.
During the delivery, it’s even easier to remove or replace some hardware or software elements so that it won’t be evident to a customer. According to some sources, many governments intercept and change different hardware products to open a backdoor.
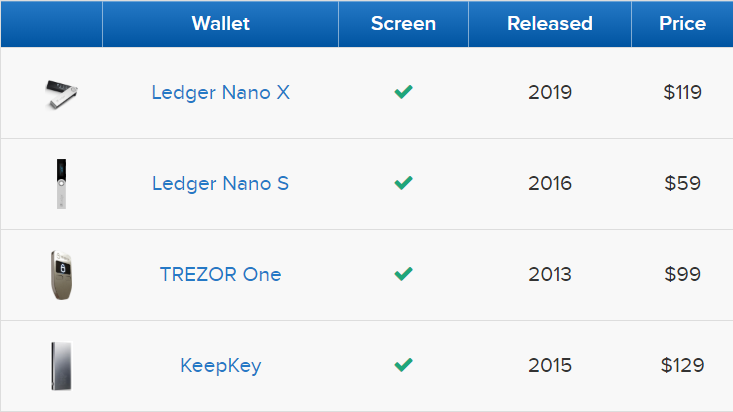
Popular Wallets Overview
Ledger Nano S
The Ledger Nano S was released in August of 2016, and alongside TREZOR, has managed to cement itself as a solid and reliable hardware wallet provider. The Ledger Nano S is the cheapest one, costing around $60. The Ledger Nano S currently supports Ark, Bitcoin, Bitcoin Cash, Dash, Dogecoin, Ethereum, Ethereum Classic, Komodo, Litecoin, PoSW, Ripple, Stratis, and Zcash.
Ledger Nano X
The Ledger Nano X is Ledgers newest hardware wallet. The main benefit is that it has Bluetooth, making it the first hardware storage that connects with iOS devices. Its more secure than using just an app on your phone because all transactions are signed with the Nano X.

KeepKey
Released in September of 2015, KeepKey rounds out the list of the more well-known commercial hardware wallets in the marketplace. It is the largest of the three hardware wallets and offers many of the same security features as TREZOR and Ledger Nano S. With a cost of around $130, KeepKey is the most expensive of the hardware devices. Cryptocurrencies currently supported by KeepKey are Bitcoin, Litecoin, Dogecoin, Namecoin, Testnet, Ethereum, and Dash.

TREZOR
TREZOR was the first ever hardware wallet to enter the marketplace in August of 2014, and has developed a good reputation for itself over time. A TREZOR device will cost you around $100 and it currently supports the following cryptocurrencies: Bitcoin, Ethereum (+ all ERC 20 tokens), Ethereum Classic, ZCash, Litecoin, Namecoin, Dogecoin, Dash, and Bitcoin Testnet.
Check out the complete tutorial to create, installing and using the Trezor hardware wallet Model T to safe your funds.

What is a Paper Wallet?
A paper wallet is another example of offline cold storage for cryptocurrencies. Private and public keys get printed on the paper wallet which can be stored in a secure place. The key is printed in the form of a QR code, which can be scanned for all transactions. It gives complete control to the user.

You should realize that it’s not the cryptocurrencies that get printed out on the paper as any other regular currency, but rather the information stored in a crypto wallet. The private key printed on the paper allows people to transfer money and consequently provides access to spending funds.
It is created using a program which randomly generates a private and public key. The keys are unique and the program generating them is open source. These keys are generated offline. This eliminates the risk of online threats.
Some argue that paper wallets will ultimately be phased out as people get more used to using bitcoin and digital ones will take over. This may be the case. For now, however, it is an excellent option if you’re concerned about security.
How to load paper wallet with a cryptocurrency?
- Use the Bitcoin address QR code for transferring Bitcoin from your software wallet to the particular address.
- After scanning the QR code transfer the Bitcoins to the address.
- You can add the number of Bitcoins loaded where “Bitcoin amount” is written and keep that safe.
- The user can generate several copies of the printed wallet and keep it as a backup.
Risks of using Paper Wallets
While paper wallets drastically decrease the threat of compromise from the hackers, they carry their own set of risks, which include-
- Fragility
The wallet is just a piece of paper. It can be easily damaged or can get worn out over time.
- Human Errors
The location of the paper can be easily forgotten, and it could be accidentally torn.
- Type of Printer Used
Non-laser printers may cause the ink to run off if the paper gets wet. Thus it is necessary to use a high-quality printer.
- Coercion
Being vocal about your crypto assets is not a wise idea. It can make the holder a vulnerable target for predators.
Why is a Hardware Wallet Better than Paper?
Paper wallets are safe if you use them the right way. While hardware ones are designed to not only store bitcoin but make it easy to use bitcoin while maintaining a high degree of security. For someone with more than one bitcoin who actually spends bitcoin frequently, hardware storage is extremely secure and convenient.
Hardware devices implement the whole secure paper wallet process in a convenient way. Offline key generation. Offline storage. Offline transaction signing.
| Hardware storage | Paper storage |
| Hardware wallets do not have full-featured software. It is not possible to download a cryptocurrency’s full blockchain on a hardware device. They also have a low storage capacity. This type of storage can’t also hold many assets, attributed to a lack of storage space. | However, with Paper wallets, storage is not an issue, since only the key pair needs to be stored on it. As a user can generate several paper copies. And transferring cryptos is as simple as handling a slip of paper to another person. |
| It supports only a limited range of cryptocurrencies. If a user buys a hardware device but wants to use an unsupported cryptocurrency, they must wait for the developers to add support for it. | Finally, if you are regularly using the currency for trading or purchasing products, it can be somewhat of a hassle to access your currency through the paper storage on each occasion and, if you’re not familiar with how they work, you could end up locking yourself out from accessing your own currency. |
What is the Safest Bitcoin Hardware Wallet?
When it comes to the best brand of hardware wallet to buy, it has to be the Ledger Nano S.
Founded in 2014, Ledger is a leader in security and infrastructure solutions for cryptocurrencies and blockchain applications. Headquartered in Paris, Vierzon and San Francisco, Ledger has a team of over 130 professionals. They specialize in developing a variety of products and services to safeguard cryptocurrency assets for individuals and companies. Among their products – the Ledger hardware storage line, already sold in 165 countries. The company has raised over $85m in 4 rounds of investments.
The Ledger Nano S is small and compact. It also has a metal casing which makes it more durable compared to other hardware wallets.

When you first plug it into your computer and set it up, you will choose a PIN to protect the device from unwanted access. Later, you will receive a 24-word seed that will be used to create your private keys. This seed should be written down in a safe place and NOT on your computer, as whoever knows this seed has control over your Bitcoins.
The Ledger Nano S has two buttons that allow you to control it. The initial setup of the device is pretty simple and takes about 3 minutes. Most of the time is spent on writing down your seed. This seed creation is one of the places where the second screen comes into play.
If your computer is compromised, a hacker will be able to see the seed if it’s displayed on your screen. This is exactly why the seed words are shown on the small device screen that is tamper-proof, so you know that only you can see your seed
The Ledger Nano S can also be used to secure existing software wallets such as MyCellium, Electrum, MyEtherWallet and more.
Another good thing is that Ledger Nano S supports over 700 coins and tokens. The main coins can be sent/received via the Ledger Live software interface.
Conclusions
Ledger Nano S vs paper wallet? To tell the truth, no method is ever truly 100% safe for storage of your currency. The ideal method would be to combine a number of options to provide the greatest level of security. Whichever method you use, make sure that you make backup provisions. Always keep backups of your details in a safe place.

